this post was submitted on 06 Oct 2024
735 points (90.8% liked)
Technology
71448 readers
2524 users here now
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related news or articles.
- Be excellent to each other!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, this includes using AI responses and summaries. To ask if your bot can be added please contact a mod.
- Check for duplicates before posting, duplicates may be removed
- Accounts 7 days and younger will have their posts automatically removed.
Approved Bots
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
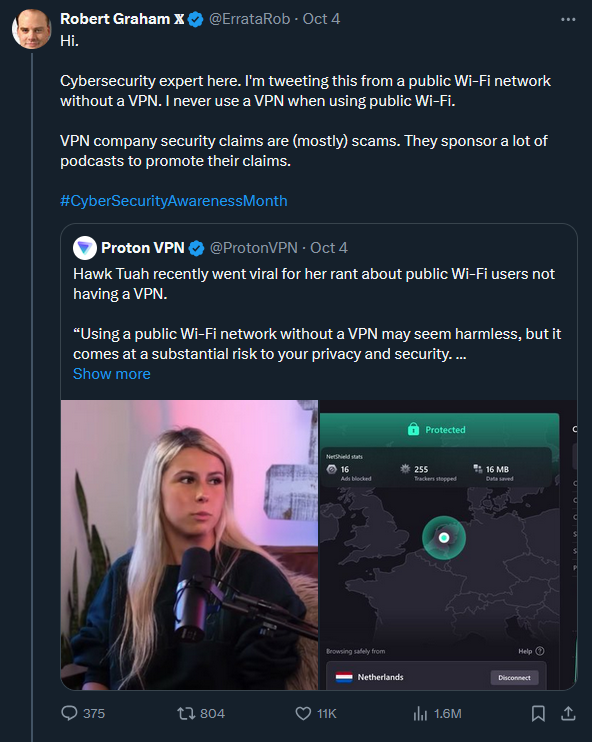
That's not a legitimate use; it's an illegal use just like piracy is.
ECH will finally fix this. https://blog.cloudflare.com/encrypted-client-hello/
SNI is still better than what we used to have. Before SNI, every site that used TLS or SSL had to have a dedicated IP address.
My understanding of the law (and yes, I read it) is that it's not illegal. The law in my state is for service providers to authenticate the ID of any state resident, it's not a requirement on the resident themselves. The service provider isn't aware what state I'm a resident of, and state law doesn't apply outside the state, so I don't know what law would be violated here.
I absolutely agree, and I actually use SNI to route packets for my homelab. Without SNI, I would have to route after handling certificates, which would be annoying because I want TLS to work within my home network, and I mess w/ DNS records to point to my local IPs when inside my network. I could have everything routed through a central hub (so one dedicated machine that handles all TLS), but that's a single point of failure, and I'm not too happy about that. Or I guess I'd have multiple IPs, and route based on which IP is being hit.
I'll have to check out ECH. Hopefully I can eat my cake and have it too.