Copied from an excellent post by sugarw0000kie on that other site. All credit for the guide to them.
Finally messed around with this and didn't see much about it, feel free to remove if breaking any rules
For this to work you'll need prowlarr, qbittorrent, and the other arrs (radarr/sonarr/readarr etc) and of course i2p router. (You could just use prowlarr to simplify searching for things without sonarr/radarr integration, then you’d just need prowlarr/qbittorrent with i2p)
In prowlarr, we need to set up proxy through i2p. So go settings-->general--> click enable proxy
This seems to work

enter your hostname (default 127.0.0.1) and port 4444 or whatever you have your http proxy set to in your i2p install. Make sure to set the ignored addresses with .com/.net etc (* denotes wildcard), so it won't request non i2p addresses through the router, otherwise i believe it will try to search any of your other indexers through i2p which is probably not good
Now you should be able to add Postman tracker like any other tracker in prowlarr as long as it's able to use your router as the proxy
aughta come up like this

From here you will need to make sure you have qbittorrent working with i2p. There is a guide floating around for this but to add to that you'll want to get the lt20 version, as the other one (i believe the default download) does not yet offer i2p support
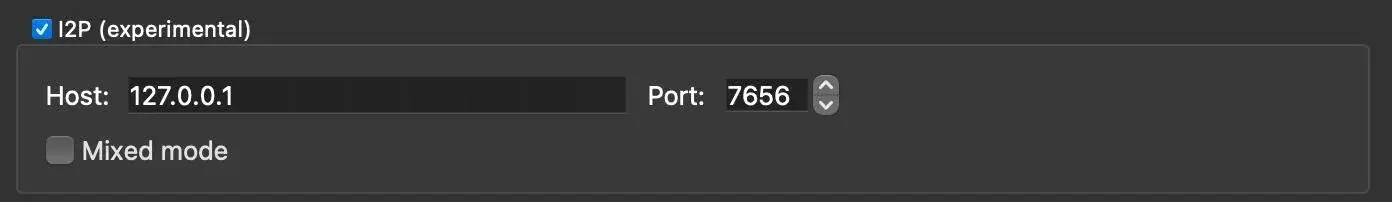
In your i2p router you'll want to make sure your SAM bridge is enabled. Then in qbittorrent go preferences-->connection and enable i2p and put in your router with hostname and port 7656 (i believe that's the default correct me if i'm wrong)
it should look like this, if you don't see this option under "Connection" you probly don't have the lt20 version
Biglybt doesn't seem to have integration with the *arrs, but assuming you have qbittorrent setup with i2p from there it's a matter of going into radarr/sonarr and adding it as a download client like normal.
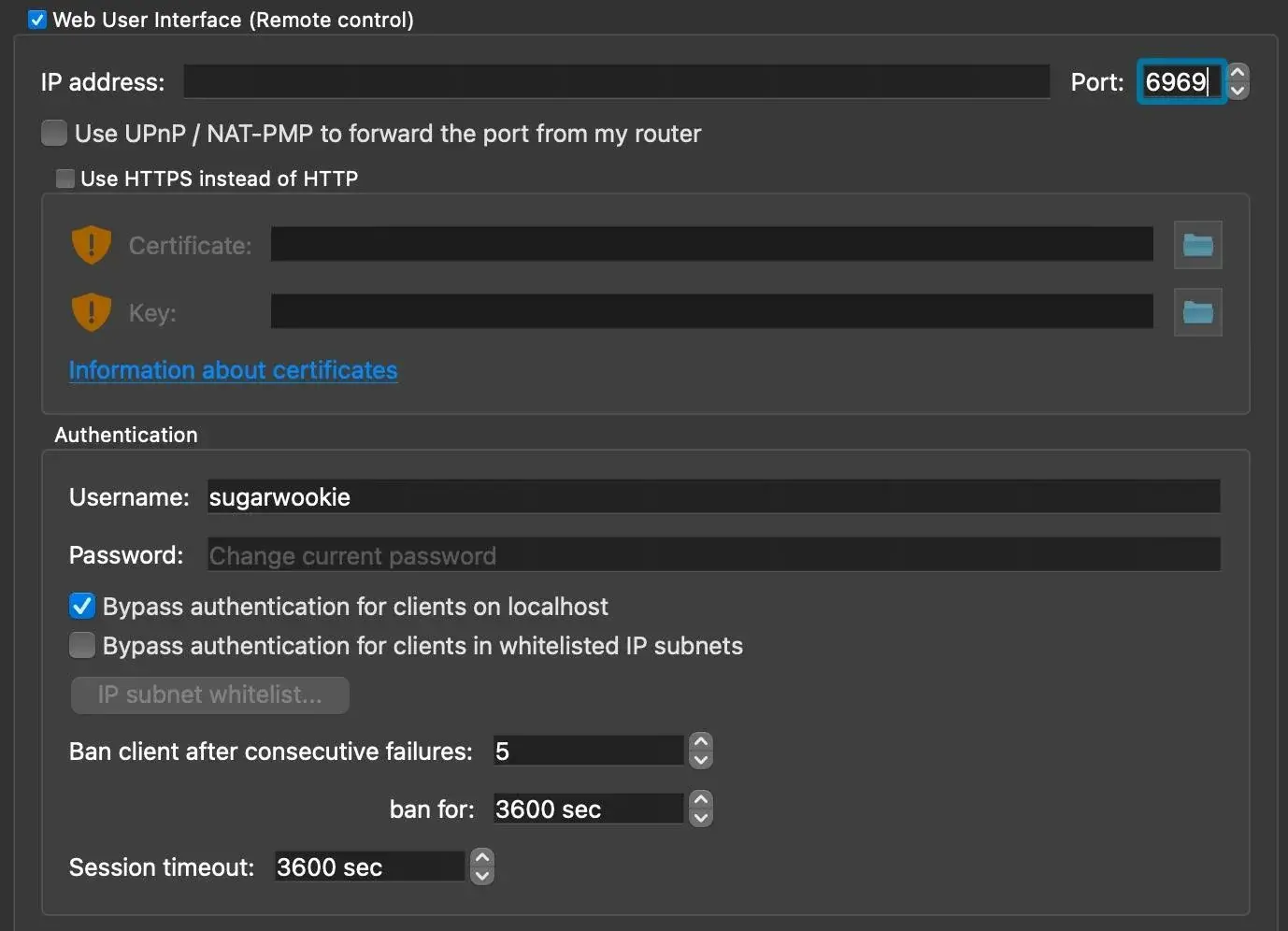
If you've never done this before, in qbittorrent under Web ui enable the web interface, should be able to leave the ip address blank (or otherwise enter how sonarr/radarr would need to access it) and enter an unused port like 6969. Put in login credentials. go to localhost:6969 or w/e you used and check that you can see the web interface from qbittorrent.
what mine looks like
on sonarr/radarr side, go settings-->download client--> and enter the ip address and port you gave it as well as the username/password. Usually helpful to add a category. Hit the test button to ensure it works
meanwhile in the *arrs

(If you just want to use prowlarr w/o sonarr radarr integration to the steps are the same to connect qbittorrent, just done in prowlarr itself. It can be used like a search engine along with all of your clearnet torrent/usenet indexers this way)
Hope this helps!





Especially with the Easy Install Bundle for Windows. Sets everything up for you.