this post was submitted on 08 Nov 2023
565 points (89.8% liked)
Technology
59148 readers
2352 users here now
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related content.
- Be excellent to each another!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, to ask if your bot can be added please contact us.
- Check for duplicates before posting, duplicates may be removed
Approved Bots
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
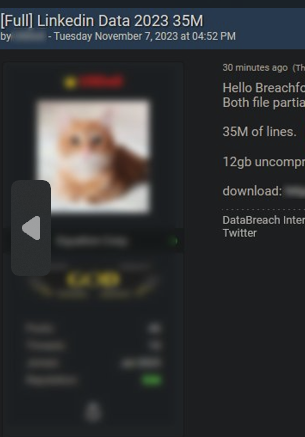
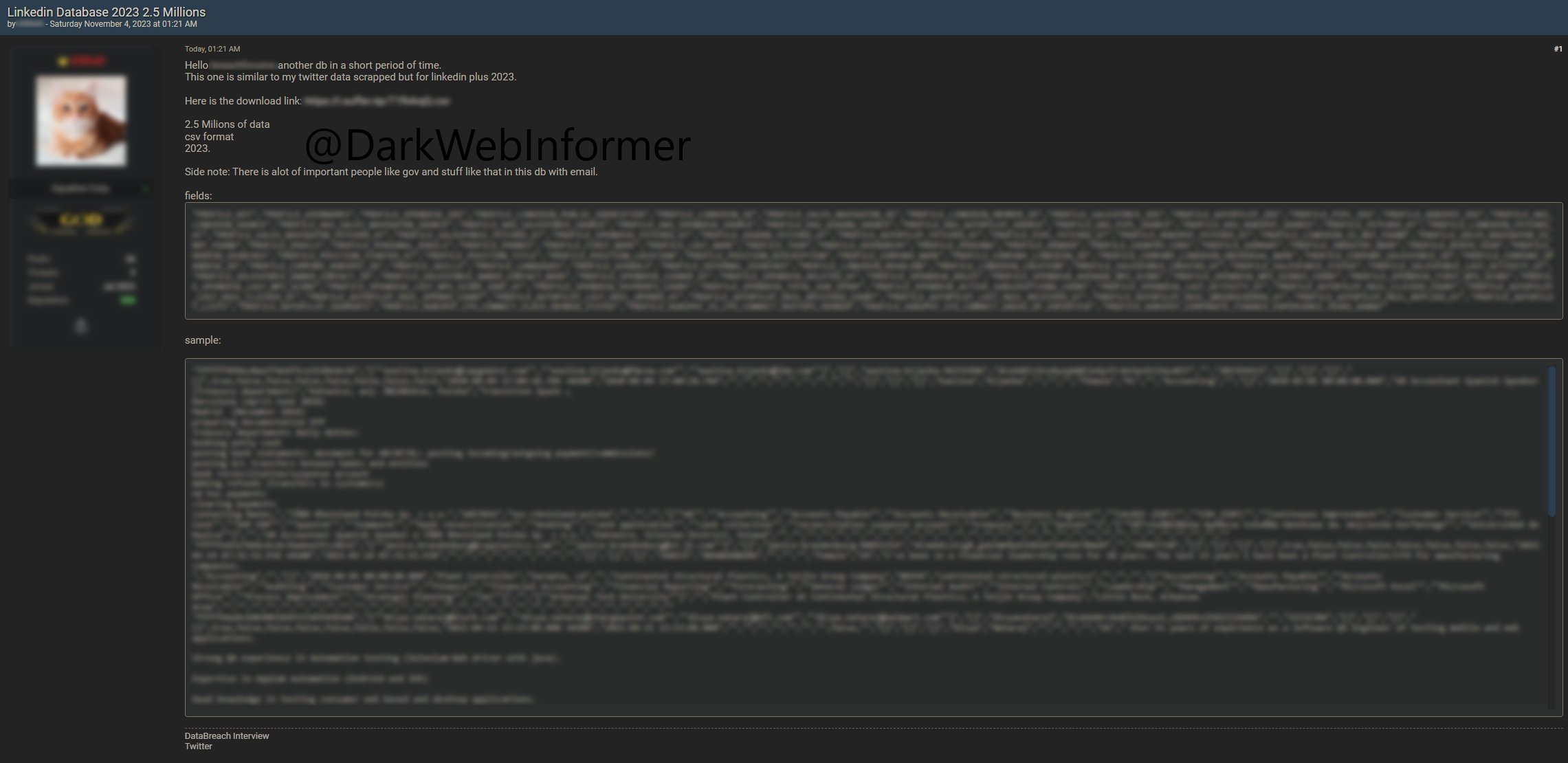
Slightly refreshing from them selling your email to spammers as soon as you signed up.
How do you mean? Are you confusing recruiters reaching out to you (which is the whole point of the platform) with spammers?
I would argue recruiters sending me mass generic emails for job offers only partially related to my field is, in fact, spam.
Agreed, but that's on the recruiters, not on the platform.
"I'll give this guy your name, contact info, and everything else I have about you, and I take no responsibility that he won't call you in the middle of the night or visit your house. All good here, yeah?" - LinkedIn
Motherfucker, if LinkedIn were one of my friends, he'd get punched every time a recruiter contacted me despite me setting my options as "not looking for jobs atm". I want you to point out the exact LinkedIn fuck whose job it is to get punched for this instead, please and thank you.
Wow, ok. Ignoring your apparent refusal to potential salary improvements, you can always turn off notifications, hibernate your account, close your account, or filter emails from LinkedIn, if it's such a big deal to you.
Nope, at one point I created a LinkedIn account and my email address immediately started getting spam.
I use unique emails for things. Technically, the emails don't even exist, but I have a rule that any email that doesn't exist will be forwarded to my actual account. So the made up email I used for LinkedIn was unique and had only ever been typed into the LinkedIn service.
I've been doing this for a while, and generally most things don't seem to lose your email. There have been a few that were probably compromised, they were safe for a while then one day they were lost - this is more likely a malicious actor accessing the website's database. However LinkedIn is one of only 2 websites I've signed up for that have instantly resulted in spam - the other was a porn website.
LinkedIn have always been shady as fuck. When they first started out, they convinced everyone to input their email login details. LinkedIn would then access your email account and send emails to all your contacts asking them to join - all coming directly from your email address, not theirs. That was how LinkedIn built its market share. Back in the MSN Messenger days, LinkedIn emails were pretty notorious, but also everyone was pretty carefree online. They were perhaps one of the first services to demonstrate that you really should be careful what you share online, even if it is a "legitimate" service. Not everyone learned that lesson.
The compromised email thing happend some time after the MSN Messenger days, and I admit that I was one of those gullible baffoons who fell for the login thing initially (I've had 3 LinkedIn accounts, my first, then the second which was unique but instantly spammed, then my current). I think the porn website was more or less around the same time as well, so it is possible that LinkedIn was compromised as well as the porn site, such that anyone who signed up for either service (and maybe some others) would instantly get added to a spam list - not by the service but by the malicious infection. However, it certainly would fit their MO for LinkedIn to just sell email addresses directly.
Nowadays, I do get emails to my current LinkedIn account email that clearly should not have been shared. These tend to be more focused on the industry I work in, instead of generic spam. Recruiters almost always contact me via messages.
Don't give LinkedIn any more information than you have to. In particular, I would encourage users to share their CV's off platform.
Thanks, it's rare to find a well thought out answer in here like yours.
I agree that LinkedIn always did shady things to increase their user base. They used dark patterns to get access to your address book even as they got constant criticism for that, both externally and internally. One of their top product managers was actually proud of that, and said that they would have done more if possible.
But I very much doubt they actually sold their customer's emails at any point. They have always been very protective of their customer's data, fighting scrapers and limiting APIs. There's no upside to selling your customers info. You're undermining your own business by doing so.
This there is the MO I was talking about.
I can't conclusively say whether or not LinkedIn intentionally sold my email, or whether they were just infected at the time. However, I feel like the former is at least as feasible, and even if it was the latter it's still reprehensible of them to be so lax in their security. Like I say, I've only experienced 2 websites that did that, and I've made up countless emails going on for years before then.
They don't have lax security. They use industry standard measures, including encryption in transit and at rest, salted passwords (they were caught without salt over a decade ago and fixed it), internal training on security, phishing simulations, the works. Your data is their business, they don't want to lose it.