If this is indeed a security feature I'm about to buy my first iPhone.
Technology
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related content.
- Be excellent to each another!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, to ask if your bot can be added please contact us.
- Check for duplicates before posting, duplicates may be removed
Approved Bots
CalyxOS and GrapheneOS have this as a feature.

Two hours seems extremely low.
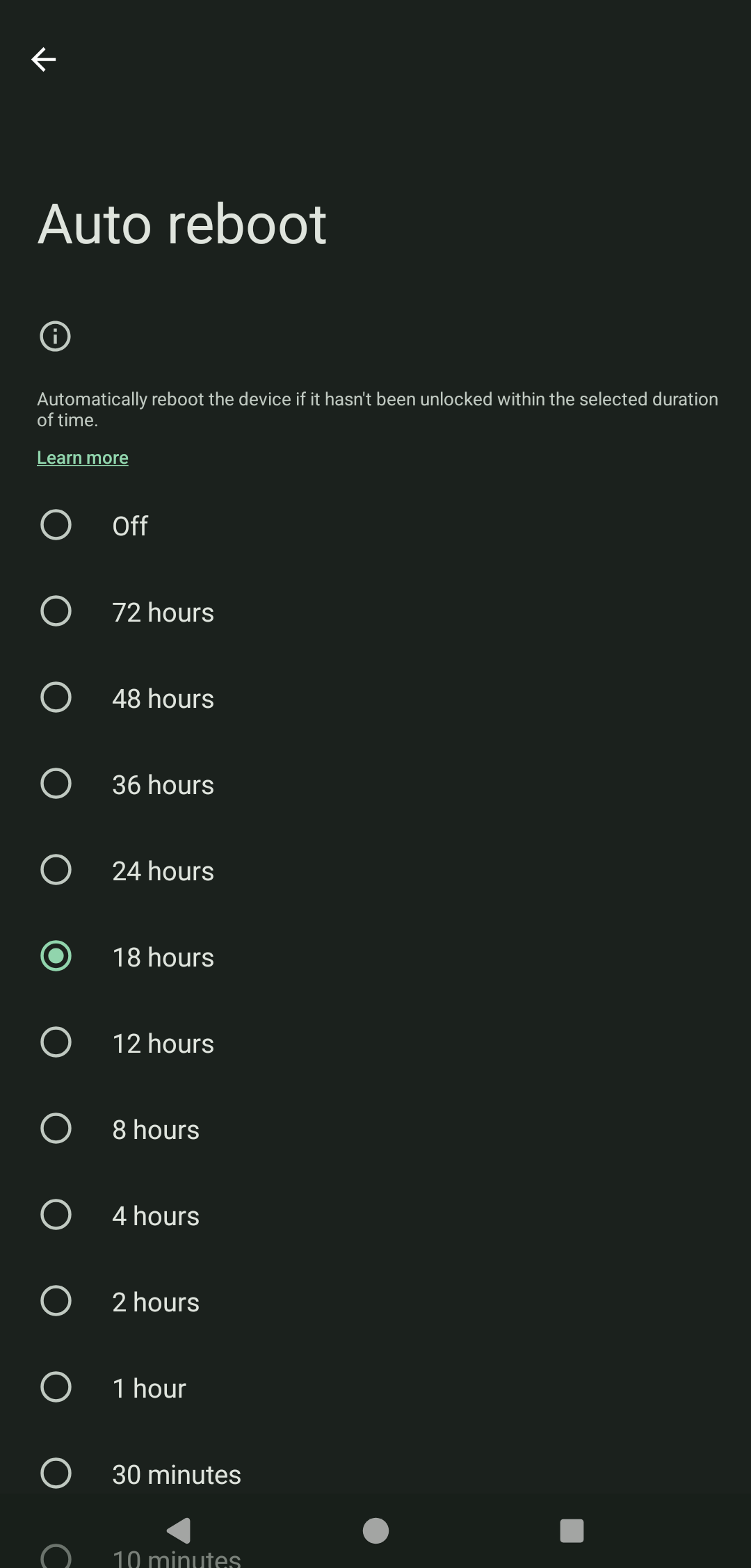
On grapheneos it's a setting, 18 hours by default I believe, but adjustable from 10 minutes to 72 hours.
That seems much more reasonable. Thanks for the info.
Wouldn't this make your phone reboot all night while you're sleeping?
Just set the time too longer than you would be asleep. So in this screenshot above you could set it to 18 hours and most people at least that I know do not go 18 hours without unlocking their phone at least one time which would then reset the timer.
Yes. Alternatively, you can just.. power it off.
I keep mine on in case of family emergencies, it's also my alarm clock
Don't switch to a privacy-violating platform just for a feature found in open source operating systems.
Oh yeah, see they've done it perfectly by having it based on the last time you unlocked your screen.
Android has it as well. It's customizable, too.
Android has an app that you can install that auto wipes a phone after X amount of time if the phone hasnt been unlocked:
https://f-droid.org/en/packages/me.lucky.wasted/
Also theres an app that allows you to set a fake password that wipes the phone:
https://f-droid.org/en/packages/me.lucky.duress/
All open source, I have tested these apps on my phones, they work great. The second app about the duress password is a bit glitchy and didnt work on some of my phones.
Disclaimer: I am not a lawyer and setting your phone to automatically wipe itself may be considered destruction of evidence in a court of law.
Thanks but I literally cannot figure out how to use these apps after installing
Nice, I think making your phone go into Before First Unlock mode cannot be considered destruction of evidence
Well they might charge you with "Obstruction of Justice" instead. Then plug it in some cellebrite device and boom, unlocked.
Best way to not have to deal with stuff like this is just to not have the incriminating evidence in the first place. If you are, for example, doing a protest, only chat with contacts in a safe place, then wipe chat logs every time, any data you wish to keep should be encrypted then uploaded anonymously via VPN/Tor and wiped from local storage. Hide the fact that such data exists so you wouldn't have a scenario where the government is trying to get you to give them the data, since they dont even know what data exists. Plausable deniability.
Edit: Those apps I've linked is still a good idea since "Destruction of Evidence" is probably a lesser charge than something like "Rioting".
Cellebrite struggles with iPhones already, this reboot is part of the cat and mouse game they’re playing
That's what they say. I mean the news literally base this off the FBI's own words, so there's no way for us to tell if they actually manage to break the encryption but then turns around that say "the encryption is too strong". Besides, iOS is closed source.
Intelligence agencies have made this "Anom Phone" that is this supposed encrypted phone that drug dealers and various criminals used to communicate, turned out to be a honeypot.
I’ve used cellebrite before.
Anecdote of 1 for you, iOS is a pain in the ass.
There are different versions.
One is where they sell the cellebrite device to law enforcement.
Another where the cellebrite device remain in control of cellebrite, and law enforcement has to send the phone to cellebrite.
Unless you actually work for cellebrite and got access to their more advanced tools, which then I doubt they would let you share the details of since that must be breaking some non-disclosure agreement.
Yes, I am well aware.
shipping a phone to them or waiting for the tech to arrive, that transit time, is what my mind went to immediately when this feature was introduced.
The phones are significantly more difficult to get into after the reboot.
I’m disclosing absolutely nothing.
Anything to make their job harder is perfectly okay by me. The only thing that would be needed would be for this to be a feature and to have a cool down period of like 48 hours where the phone would reboot twice in that time so that if it was held it would still reboot itself.
Edit: Even better idea. Turning off the feature requires a reboot.
Note to those wishing for such a function, it’s possible by creating an iOS Shortcut - New Shortcut > Shutdown > Change it to ‘Restart’.
From there, you create an automation in Shortcuts to run based on time, location, etc.
Alas, it asks if you want to restart.
You could always take 10 seconds and invoke the operating system's hard shutdown command if you have the 10 seconds to spare. On Android at least, that's pressing and holding power and volume up for 10 seconds. But I do not know what it would be on the iPhone.
this is the police we're talking about, they probably just forgot to charge them and are trying to shift the blame
Whatever it is, incompetence, bug, or feature, I love it.
Speculation is that ios 18 is communicating with other phones while locked to determine security. This can more likely be a NSA/US empire backdoor than a user protection feature. Lowly police systems are just not on the "hacker list". One way the backdoor could work is that if a "NSA/Mossad list phone" is present, protect the other phones, unless the phones are in an NSA/Mossad secure facility.
Or it could just be using the inactivity reboot feature that was recently added to iOS.
ok. I'd suspect spy agency back doors if the feature was unannounced. If it was an announced feature, then that is reasonable explanation.
It’s literally a documented feature AND it’s weird super secret spy agency shit is the easiest answer for you tbh.
I thanked you for explanation. OP did not suggest that as an explanation.
You did though. Lmao
Hot take: this is actually a bug not a feature.
Which is the saddest part, honestly. If it was a feature, that would be fantastic news. And especially if it had a cooldown feature of like 48 hours, where it would reboot twice in that timeframe, so that if a cop turned off the setting, while it was in their possession, it wouldn't matter because it would reboot anyway.
Someone said it in another thread yesterday, baseband memory leak. The firmware for that shit is terrible, I've had to deal with it in the past.
"new security feature" "warning"
🙂