Wow, this is a very complex exploit, involving bits of iMessage and an undocumented CPU feature that allowed the attacker to evade hardware memory protection. From what I can see, Lockdown mode would have prevented this. The attacker is ridiculously skilled regardless
Exerpts from the article missing from the bot summary:
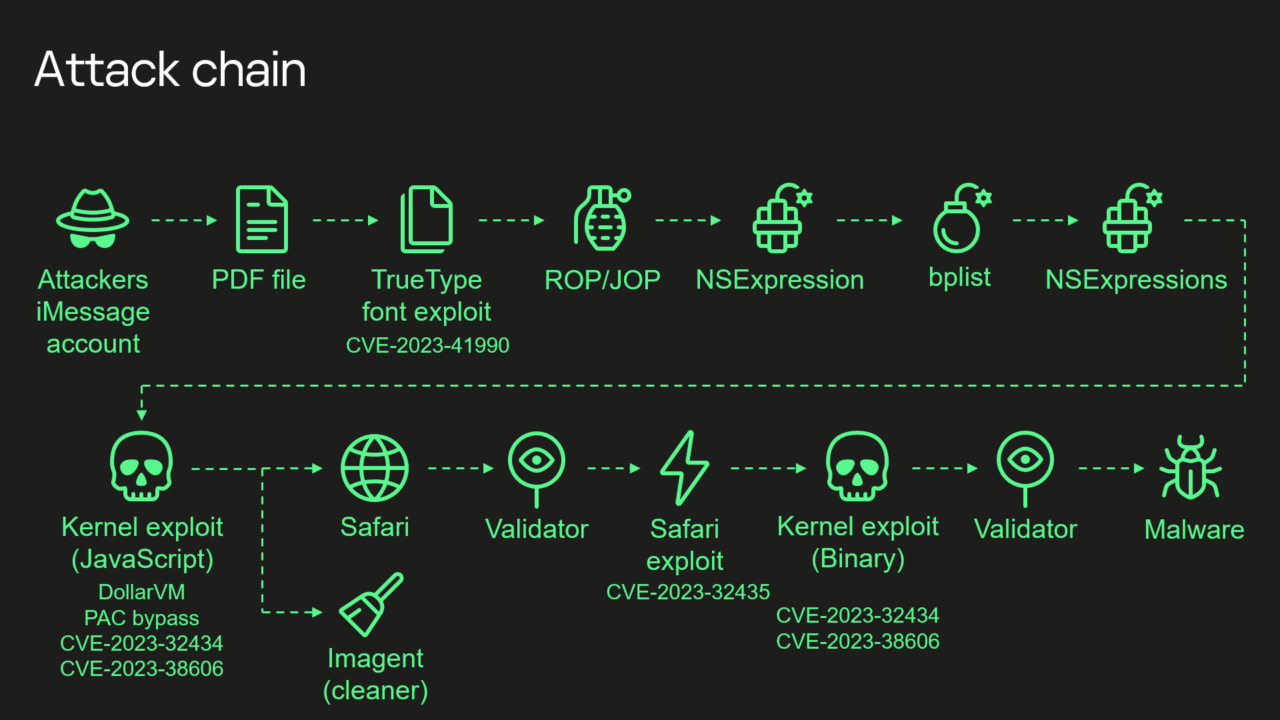
The mass backdooring campaign, which according to Russian officials also infected the iPhones of thousands of people working inside diplomatic missions and embassies in Russia, according to Russian government officials, came to light in June. Over a span of at least four years, Kaspersky said, the infections were delivered in iMessage texts that installed malware through a complex exploit chain without requiring the receiver to take any action.
With that, the devices were infected with full-featured spyware that, among other things, transmitted microphone recordings, photos, geolocation, and other sensitive data to attacker-controlled servers. Although infections didn’t survive a reboot, the unknown attackers kept their campaign alive simply by sending devices a new malicious iMessage text shortly after devices were restarted.
The most intriguing new detail is the targeting of the [...] hardware feature [...]. A zero-day in the feature allowed the attackers to bypass advanced hardware-based memory protections designed to safeguard device system integrity even after an attacker gained the ability to tamper with memory of the underlying kernel.